Mastering Crypto Security: An Expert's Guide to Safeguarding Your Digital Assets

The ever-expanding world of cryptocurrency investing presents numerous opportunities for seasoned and novice investors. However, the digital landscape also attracts hackers and scammers, making it crucial for investors to prioritize security. In 2022, according to the "Crypto Crime Report" published by Chainalysis, the cryptocurrency market experienced significant turmoil, with several major firms collapsing amid fraud allegations. Despite the market downturn, illicit transaction volumes reached an all-time high of $20.1 billion. This figure is expected to grow as more addresses associated with illicit activities are identified. Notably, 44% of the illicit transaction volume in 2022 was linked to sanctioned entities.
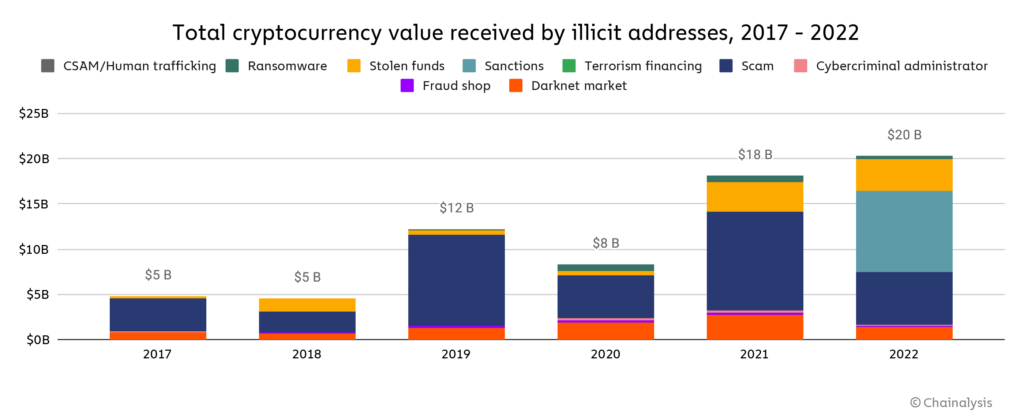
While transaction volumes decreased across most conventional categories of cryptocurrency-related crime, stolen funds saw a 7% increase year-over-year. The market downturn may have contributed to this, as crypto scams tend to generate less revenue during bear markets. Overall, the share of all cryptocurrency activity linked to illicit activity rose for the first time since 2019, from 0.12% in 2021 to 0.24% in 2022.
Understanding the Fundamentals of Cryptocurrency Security
A solid foundation in cryptocurrency security begins with understanding the basics:
- Private keys: These are unique alphanumeric codes that grant you access to your digital assets. Safeguarding private keys is of utmost importance.
- Wallets: Digital wallets store your cryptocurrencies and private keys. Wallets can be hardware-based (physical devices) or software-based (apps or online platforms).
- Two-factor authentication (2FA): This additional security layer requires a secondary method of authentication, such as a code sent to your phone, to access your account.
Selecting a Secure Wallet
There are several wallet options available, each with its pros and cons:
- Hardware wallets: These physical devices store your private keys offline, making them less susceptible to hacking. Examples include Trezor and Ledger.
- Software wallets: These wallets are apps or online platforms that can be accessed on your devices. While convenient, they are more vulnerable to cyberattacks than hardware wallets.
Choose a wallet with a strong security reputation, and always keep your wallet software up to date.
Safeguarding Private Keys and Recovery Phrases
Your private keys and recovery phrases are the keys to your digital assets. Protect them by following these guidelines:
- Never share your private keys or recovery phrases with anyone.
- Store them offline in a secure location, such as a safety deposit box or a fireproof safe.
- Consider using a hardware wallet, which provides added security by keeping private keys offline.
Implementing Two-Factor Authentication (2FA)
Enable 2FA on all your cryptocurrency accounts, including exchanges and wallets. Use authenticator apps like Google Authenticator or Authy instead of SMS-based 2FA, as SMS can be vulnerable to SIM-swapping attacks.
Choosing Reputable Exchanges and Platforms
Select exchanges and platforms with a proven track record of security and legitimate trade volumes. Top-tier exchanges like Coinbase, Kraken, Bitstamp, and Gemini are known for their security measures.
Diversifying Your Crypto Holdings
Avoid keeping all your digital assets in one place. Diversify your holdings across multiple wallets, exchanges, and storage methods to reduce risk.
Conducting Thorough Research
Stay informed about the latest security trends and vulnerabilities. Be cautious of new projects and investment opportunities, and always verify the credibility of the individuals or organizations behind them.
Staying Vigilant Against Scams and Phishing Attacks
Be wary of unsolicited emails or messages containing suspicious links or requests for personal information. Double-check URLs to ensure you're on legitimate websites, and never enter sensitive information on unsecured sites.
Regularly Monitoring Your Accounts and Transactions
Keep a close eye on your accounts and transactions for any unusual activity. Promptly report any suspicious activity to the relevant exchange or platform.
Educating Yourself on Crypto Security Best Practices
Stay updated on the latest security best practices and implement them to protect your digital assets. Engage with the crypto community to learn from others' experiences and share your knowledge.
Conclusion
The rapidly evolving world of cryptocurrency investing offers immense potential for gains, but it also exposes investors to a myriad of risks. Following this comprehensive guide and diligently implementing the suggested security measures, you can safeguard your digital assets and confidently navigate the crypto landscape. Stay vigilant, continue to educate yourself on the latest security best practices, and always prioritize the protection of your investments. Embrace the exciting opportunities that cryptocurrency has to offer while maintaining a strong focus on security and risk management
Disclaimer
*The information and analysis provided in this article are intended for educational and informational purposes only and should not be considered as financial, investment, or professional advice. While our team strives to ensure the accuracy and reliability of the content, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability of the information presented.
The content within this article may include opinions and forward-looking statements that involve risks and uncertainties. The blockchain and cryptocurrency markets are highly volatile, and past performance is not indicative of future results. Any reliance you place on the information presented is strictly at your own risk. Before making any investment decisions, we highly recommend consulting with a qualified financial advisor or conducting your own thorough research.
By accessing and using the information provided in this article, you acknowledge and agree that neither the authors, publishers, nor any other party involved in the creation or delivery of the content shall be held liable for any direct, indirect, incidental, consequential, or punitive damages, including but not limited to loss of profits, goodwill, or data, arising out of your use or inability to use the information provided or any actions you take based on the information contained within this section.*





